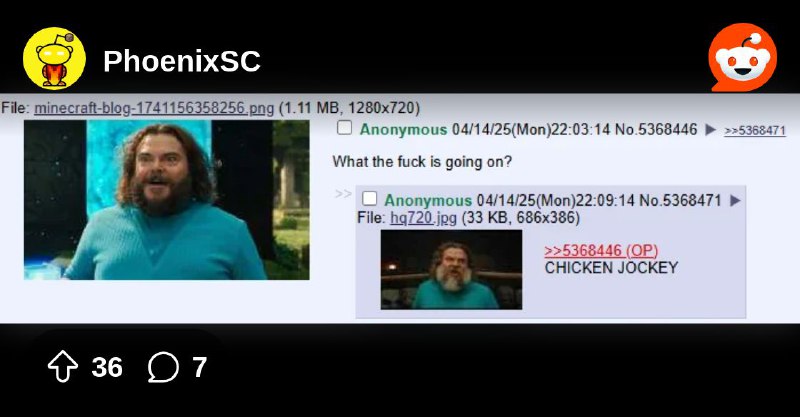
Aparentemente o 4chan.org foi hackeado novamente, por um time rival
"View it on an archive cause that shit is not gonna load. Yes it was actually the last thing posted before the servers crashed https://desuarchive.org/qa/thread/5368446/#5368471"
Discussão: https://www.reddit.com/r/PhoenixSC/comments/1jzm7oe/this_is_the_final_post_on_4chan_before_the_site/
"View it on an archive cause that shit is not gonna load. Yes it was actually the last thing posted before the servers crashed https://desuarchive.org/qa/thread/5368446/#5368471"
Discussão: https://www.reddit.com/r/PhoenixSC/comments/1jzm7oe/this_is_the_final_post_on_4chan_before_the_site/
Fonte: https://www.bleepingcomputer.com/news/security/ssl-tls-certificate-lifespans-reduced-to-47-days-by-2029/
Opinião da comunidade no Reddit: https://www.reddit.com/r/sysadmin/comments/1jvqxre/ssl_certificate_lifetimes_are_really_going_down/
Link oficial da discussão da alteração no grupo da Google:
https://groups.google.com/a/groups.cabforum.org/g/servercert-wg/c/bvWh5RN6tYI?pli=1
Nesse vídeo o Naham mostra como é o ApiSecUniversity por dentro e na prática.
https://www.youtube.com/watch?v=6Tyqvl-GSNQ
https://www.youtube.com/watch?v=6Tyqvl-GSNQ
Saiu um plugin que permite usar MCP:
https://www.linkedin.com/posts/jafar-pathan_jadx-reverseengineering-plugin-ugcPost-7316955261347282946-qJL1
A simplier implementation of a Damn Vulnerable MCP Server that adds two or more numbers
https://github.com/pfelilpe/DVMCP
https://github.com/pfelilpe/DVMCP
Live Hacking Talks de 4 meses atras, mas vale a pena:
https://www.youtube.com/live/BKXfrNwrcqQ
https://www.youtube.com/live/BKXfrNwrcqQ
Os ingressos foram liberados as 15hs do dia 10/04/25
17 mai - 2025 • 14:30 > 18 mai - 2025 • 20:00
Evento presencial em Hotel Nacional Inn Jaraguá São Paulo by Nacional Inn, São Paulo - SP
https://www.sympla.com.br/evento/security-bsides-sao-paulo-bsidessp-2025/2909027
Já usou o nuclei, katana, subfinder, nuclei httpx, naabu? Tudo ferramenta desenvolvida por esse time.
Só que tem muito mais. Eles tem várias ferramentas que não foram pro mainstream e que são muito uteis.
Então antes de sair desenvolvendo algo do zero, dá uma sacada lá.
Pra quem conhece o interact-sh via terminal, por exemplo, eles tem até a versão web:
Publicado há 1 hora
https://www.youtube.com/watch?v=w1J01QNT5cY
https://www.youtube.com/watch?v=w1J01QNT5cY
Episode 118 is out! In this episode Justin and Joseph discuss security news including clientside tidbits, "Credentialless" iframes, prototype pollution, and polyglots in llms.txt
https://www.youtube.com/watch?v=DWczX_1t_x4
https://www.youtube.com/watch?v=DWczX_1t_x4
Faz tempo mas eu não tinha visto essa pesquisa
Next.js and cache poisoning: a quest for the black hole
https://zhero-web-sec.github.io/research-and-things/nextjs-and-cache-poisoning-a-quest-for-the-black-hole
Next.js and cache poisoning: a quest for the black hole
https://zhero-web-sec.github.io/research-and-things/nextjs-and-cache-poisoning-a-quest-for-the-black-hole